Cracking passwords can be a bit tricky for most of us, well unless you are the infamous Johnny Ramensky. Just kidding. But here is the thing, with the right tools and procedure, you can crack any password. I'm a noob when it comes to password cracking and coding in general so I found it interesting after going through many resources just to find the right way to do this task given to us by Alx SWE and I thought it good to share what I learned through the process.
In the crackme4 file, only one Hint is provided: The program prints “OK” when the password is correct. Well, of course, the file is password protected and we have to find the password.
There are several tools used to convert a Python bytecode to a Python file and to mention a few we have uncompyle6, pycdc3, decompyle3 and many more. These tools can be very useful for reverse engineering and understanding the code from a compiled Python bytecode. Let us focus on Uncompyle6. First of all, we need to install it.

Done, we now have to find the contents of our file, and to do this we run the ls command with the l flag. thus ls -l.

From the file permissions above, observe that this is not an executable file so we need to further investigate our file and see what type it is. thus we run the file command in the terminal:

The output from the file command tells us that crackme4 is a byte-compiled Python file compiled by Python 3.4.
The bytecode is a low-level platform-independent representation of your source code.
Understanding that the file is in bytecode and needs to be translated to a Python file, we get back to the beloved uncompyle6 and run the following command. $ uncompyle6 crackme4 > crackme4.py
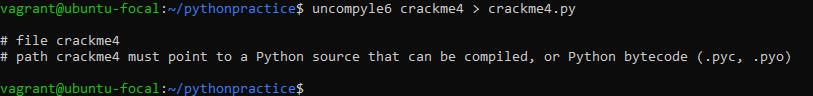
As you can see, the output is in comment form. What it tells us is the comment is related to the file named crackme4 and goes on to clarify that the acceptable formats for the crackme4 file should either be a Python source file (with a .py extension) that can be compiled and executed directly by the Python interpreter, or a Python bytecode file (with a .pyc or .pyo extension) that contains pre-compiled Python code.

Getting more and more interesting I know, so let us rename it and find out. we pass the following commands.

If we do an ls we realize that we now have 3 files. the crackme4 file, crackme.pyc and crackme.py files. Interesting, because now we have been able to successfully decompile our file.
If we run the file .py and input a random password. Oops, dead. KO.

Well, using your favorite text editor vim(I know this may cause an uprising from team Emacs but as the saying goes irriz what irriz.) let us examine our file. Maybe there is a hint inside. We run:$ vim crackme4.py.

From the above source code, there are at least 3 distinguishing things. The comments, variables and of course the if...else loop. Observing the comment let us break down what they mean. line 1 is the version I am using of uncompyle6, line 2 indicates that the bytecode was generated with Python version 3.4, lines 3 and 4 show information on the Python and GCC versions used during decompilation, line 5 indicates the source file name while line 7 indicates the date and time when the source code was compiled into bytecode.

Satisfaction! Yes!!. That is the word. Now examining further to line 8, the line prompts the user to enter a password and assigns the input to the variable 'pwd'. Line 9 initializes the variable 'ok' with a string value "Zen of Python". Line 10 further concatenates the string "C" to the value 'ok'. Now we have "Zen of Python C"
The variable 'ok' is further manipulated by performing several operations.
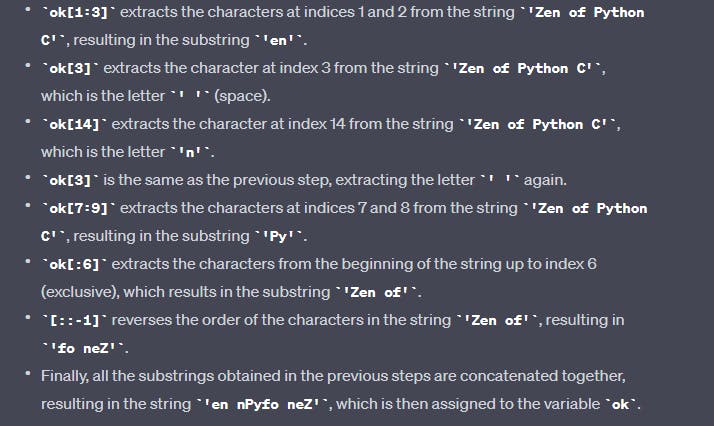
The line print(ok) then prints the value of the variable ok, which is 'en C Pyfo neZ'.
Isn't it amazing. For now, we not only have our password but also completed our task. Running the command.

Well, that's it for now. Karibu.

